
In the world of DeFi, Liquid Staking has surpassed decentralized exchanges (DEXs) to achieve the highest Total Value Locked (TVL). Liquid Staking Token (LST) protocols manage substantial assets, significantly impacting the security and functionality of their underlying Proof-of-Stake (PoS) chains.
Bifrost's cross-chain architecture enhances the interoperability and efficiency of DeFi applications. However, effective cross-chain communication and seamless user experiences require a robust security framework. Bifrost addresses this need with a comprehensive security model that protects staked assets and maintains network integrity.
The Bifrost Polkadot and Bifrost Kusama chains are parachains of Polkadot and Kusama, respectively. Their security and resistance to reorganization are protected by the relay chain.
As widely known, Polkadot employs a shared architecture where the relay chain randomly assigns validators to parachains and verifies their blocks. The blocks of the relay chain will include the blocks of the parachain, providing data availability for the parachains. This mechanism is the foundation of Polkadot's shared security.
Parachains do not require running validators, nor do they need to increase validator numbers to promote decentralization. Instead, they operate with a limited number of collator nodes. The role of collator nodes functions similarly to the Sequencer in Ethereum L2, which is responsible for collecting and ordering transactions in the parachains. The number of collators does not need to be excessive; it only needs to ensure network availability and make transactions less prone to censorship. Currently, the Bifrost Polkadot chain has over 32 collator nodes, which is more than sufficient to maintain robust network performance.
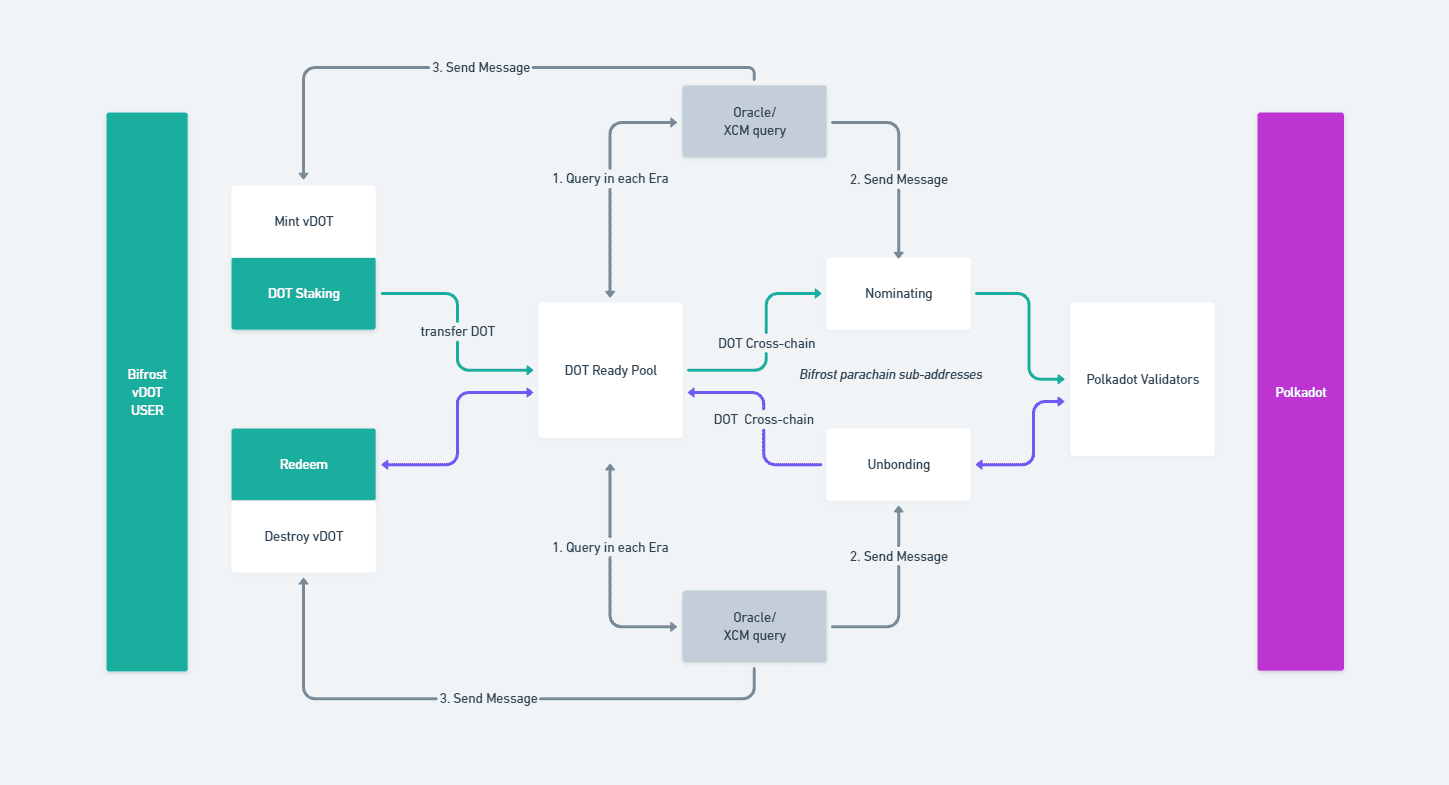
In Bifrost's cross-chain architecture, there's a significant involvement of cross-chain communication. The security of cross-chain bridges is a well-known challenge in the blockchain space. So, how does Bifrost ensure the security of cross-chain communication? The answer lies in the cross-chain communication mechanism of Polkadot. Polkadot aims not only to create a platform for shared security but also to achieve seamless cross-chain interoperability. Polkadot accomplishes this through the Cross-Chain Message Passing (XCMP) protocol and the Cross-Consensus Message (XCM) format.
In summary, XCMP ensures fast, secure, ordered, and cost-effective cross-chain message delivery between Polkadot parachains.
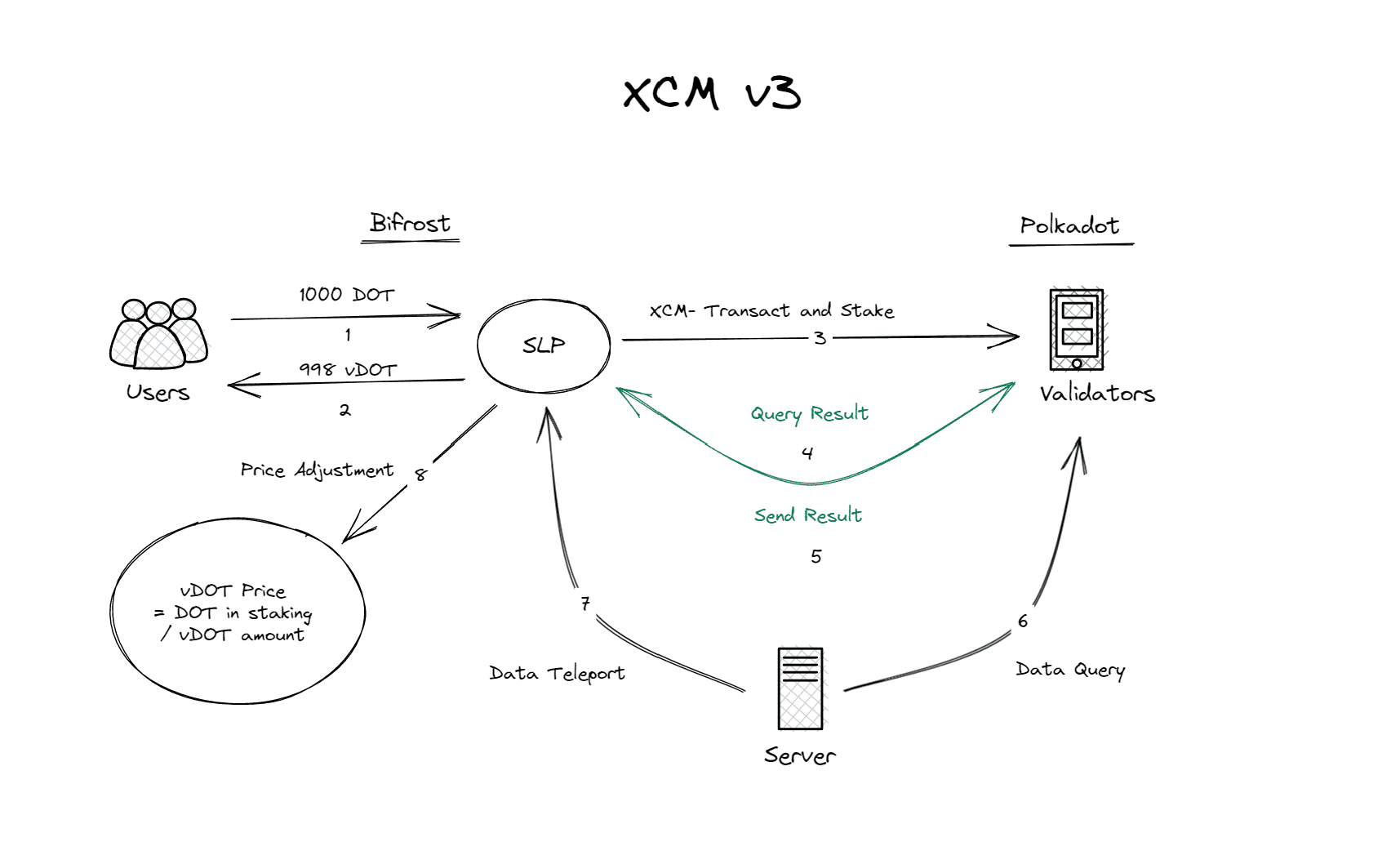
When XCMP is used for communication between parachains, XCM is used to ensure that these chains can understand each other's messages and know how to execute them. Polkadot's vision for XCM extends beyond the cross-chain communication within Polkadot. It aims to be adopted by a broader range of heterogeneous blockchains. Therefore, it is named the Cross-Consensus Message format.
For a more in-depth interpretation of the operational mechanisms of XCMP and XCM, Bifrost provides detailed insights in this article: How Bifrost Supports vMOVR and vGLMR Based on XCM.
However, Bifrost also acknowledges that heterogeneous cross-chain infrastructure is currently not mature. Therefore, it has not opted for a radical approach to fully implement the cross-chain architecture but instead retained the SLP modules on Ethereum and Kusama. Nevertheless, as the cryptocurrency industry develops, secure and reliable heterogeneous cross-chain solutions are expected to emerge.
Bifrost adopts a fully decentralized approach to manage staked assets. All processes are completed through decentralized contracts or runtime, without any human intervention and the need to trust any third party, including the Bifrost development team.
Furthermore, Bifrost's on-chain code is open source, allowing for public scrutiny and vulnerability reporting. The code has been rigorously audited by multiple security firms, including Beosin, Slowmist, and TokenInsight. Since its inception in 2019, Bifrost has maintained a flawless security record, demonstrating its resilience in terms of code security.
Apart from the risks of intentional misconduct and code vulnerabilities, users' staked assets may also face the risk of slashing. Staked assets essentially serve as collateral for running nodes. If a node engages in improper behavior that disrupts the network, a portion or all of the malicious node's staked funds may be slashed by the network.
An LST protocol that selects validators irresponsibly can expose LST asset holders to slashing losses, which could manifest as a decrease in the exchange rate between LST and the original token.
To minimize users' exposure to slashing losses, Bifrost has implemented several measures:
For a more detailed explanation of how Bifrost distributes, mitigates, and compensates for slashing risks, refer to How Bifrost provides an insurance mechanism for vToken holders against the Slash risk.
Bifrost's security model is a testament to its commitment to protecting staked assets and ensuring the reliability of its network. By leveraging Polkadot's shared security, implementing a non-custodial approach, conducting rigorous code audits, and establishing robust slash protection mechanisms, Bifrost provides a secure environment for DeFi activities.